K8S与harbor的集成
前提:K8s集群已经部署完成 version: K8s: v1.14 docker-ce: v18.09
1.安装Harbor
1.1 下载docker-compose
[root@t71 harbor]# wget https://github.com/docker/compose/releases/download/1.17.0-rc1/docker-compose-Linux-x86_64
[root@t71 harbor]# chmod +x docker-compose-Linux-x86_64
[root@t71 harbor]# mv docker-compose-Linux-x86_64 /usr/bin/docker-compose
1.2 下载harbor
[root@t71 harbor]# wget https://storage.googleapis.com/harbor-releases/release-1.7.0/harbor-offline-installer-v1.7.4.tgz --no-check-certificate
[root@t71 harbor]# tar xvf harbor-offline-installer-v1.7.4.tgz
[root@t71 harbor]# docker load -i harbor.v1.7.4.tar.gz
1.3 生成证书
[root@t71 ssl]# vim harbor-csr.json
{
"CN": "harbor",
"hosts": [
"127.0.0.1",
"192.168.4.71"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "System"
}
]
}
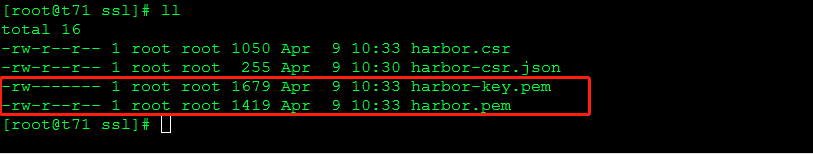
[root@t71 ssl]# cfssl gencert -ca=/k8s/kubernetes/ssl/ca.pem -ca-key=/k8s/kubernetes/ssl/ca-key.pem -config=/k8s/kubernetes/ssl/ca-config.json -profile=kubernetes harbor-csr.json | cfssljson -bare harbor
1.4 编辑harbor.cfg
cfg中参数的详细说明见:github.com/goharbor/ha…
[root@t71 harbor]# cat harbor.cfg | grep -v "#"
_version = 1.7.0
hostname = 192.168.4.71 ## hostIP
ui_url_protocol = https ## 默认是http,如果该为https,需要修改对应的ssl_cert和ssl_cert_key字段
max_job_workers = 10
customize_crt = on
ssl_cert = /k8s/harbor/ssl/harbor.pem
ssl_cert_key = /k8s/harbor/ssl/harbor-key.pem
secretkey_path = /data
admiral_url = NA
log_rotate_count = 50
log_rotate_size = 200M
http_proxy =
https_proxy =
no_proxy = 127.0.0.1,localhost,core,registry
email_identity =
email_server = smtp.mydomain.com
email_server_port = 25
email_username = sample_admin@mydomain.com
email_password = abc
email_from = admin <sample_admin@mydomain.com>
email_ssl = false
email_insecure = false
harbor_admin_password = Harbor12345
auth_mode = db_auth
ldap_url = ldaps://ldap.mydomain.com
ldap_basedn = ou=people,dc=mydomain,dc=com
ldap_uid = uid
ldap_scope = 2
ldap_timeout = 5
ldap_verify_cert = true
ldap_group_basedn = ou=group,dc=mydomain,dc=com
ldap_group_filter = objectclass=group
ldap_group_gid = cn
ldap_group_scope = 2
self_registration = on
token_expiration = 30
project_creation_restriction = everyone
db_host = postgresql
db_password = root123
db_port = 5432
db_user = postgres
redis_host = redis
redis_port = 6379
redis_password =
redis_db_index = 1,2,3
clair_db_host = postgresql
clair_db_password = root123
clair_db_port = 5432
clair_db_username = postgres
clair_db = postgres
clair_updaters_interval = 12
uaa_endpoint = uaa.mydomain.org
uaa_clientid = id
uaa_clientsecret = secret
uaa_verify_cert = true
uaa_ca_cert = /path/to/ca.pem
registry_storage_provider_name = filesystem
registry_storage_provider_config =
registry_custom_ca_bundle =
[root@t71 harbor]#
1.5 安装
[root@t71 harbor]# ./install.sh
1.6 登陆web页面
初始值username/password:admin/Harbor12345
2. k8s与harbor集成
2.1 创建secret
2.1.1 命令行
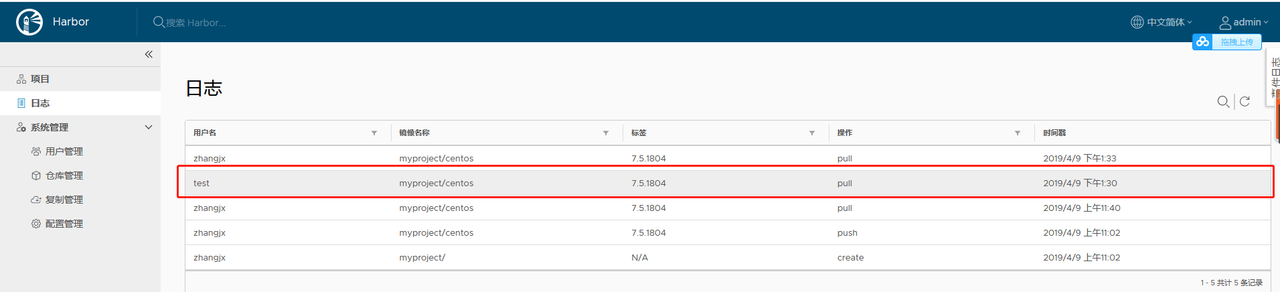
kubectl create secret docker-registry registry-secret --namespace=default --docker-server=192.168.4.71:80 --docker-username=test --docker-password=Test12345 --docker-email=test@qq.com
- registry-secret: secret的名称
- docker-server: 登陆harbor页面的ip
- docker-username:为harbor中的username
- docker-password:为harbor中用户对应的password
- docker-email:为harbor中用户对应的email地址
2.1.2 yaml文件
[root@t71 harbor]# echo "test:Test12345" | base64
dGVzdDpUZXN0MTIzNDUK
[root@t71 harbor]# vim dockerconfig.json
{
"auths": {
"192.168.4.71:80": {
"auth": "dGVzdDpUZXN0MTIzNDUK",
"email": "test@qq.com"
}
}
}
[root@t71 harbor]# cat dockerconfig.json | base64 -w 0
ewogImF1dGhzIjogewogICAiMTkyLjE2OC40LjcxOjgwIjogewogICAgICAiYXV0aCI6ICJkR1Z6ZERwVVpYTjBNVEl6TkRVSyIsCiAgICAgICJlbWFpbCI6ICJ0ZXN0QHFxLmNvbSIKICAgfQogfQp9Cg==[root@t71 harbor]#
[root@t71 harbor]# vim secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: registry-secret
namespace: default
data:
.dockerconfigjson: ewogImF1dGhzIjogewogICAiMTkyLjE2OC40LjcxOjgwIjogewogICAgICAiYXV0aCI6ICJkR1Z6ZERwVVpYTjBNVEl6TkRVSyIsCiAgICAgICJlbWFpbCI6ICJ0ZXN0QHFxLmNvbSIKICAgfQogfQp9Cg==
type: kubernetes.io/dockerconfigjson
新添加ServiceAccout来包装Secret,使得不必对每个pod中的image都单独进行镜像拉取密码的操作。(K8s inaction上面提到的)
[root@t71 harbor]# vim my-service-accout.yaml
apiVersion: v1
kind: ServiceAccout
metadata:
name: my-service-accout
imagePullSecrets:
- name: registry-secret
kubectl create -f my-service-accout.yaml
[root@t71 harbor]# vim test.yaml
apiVersion: v1
kind: Pod
metadata:
name: centos-pod
namespace: default
spec:
serviceAccoutName: my-service-accout
containers:
- name: centos
image: 192.168.4.71:80/myproject/centos:7.5.1804
command: ['/usr/sbin/init']
2.1.3 创建pod
[root@t71 harbor]# vim test.yaml
apiVersion: v1
kind: Pod
metadata:
name: centos-pod
namespace: default
spec:
containers:
- name: centos
image: 192.168.4.71:80/myproject/centos:7.5.1804
command: ['/usr/sbin/init']
imagePullSecrets:
- name: registry-secret
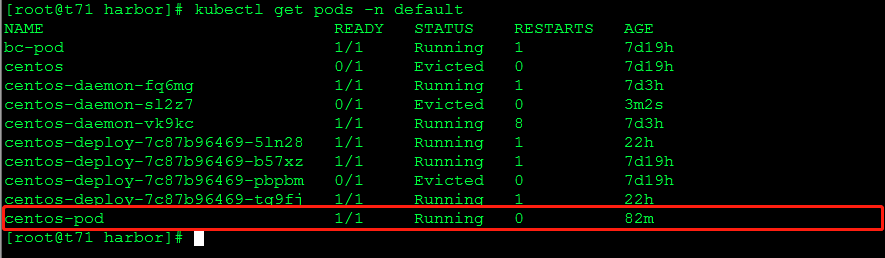
kubectl create -f test.yaml
kubectl get pods -n default
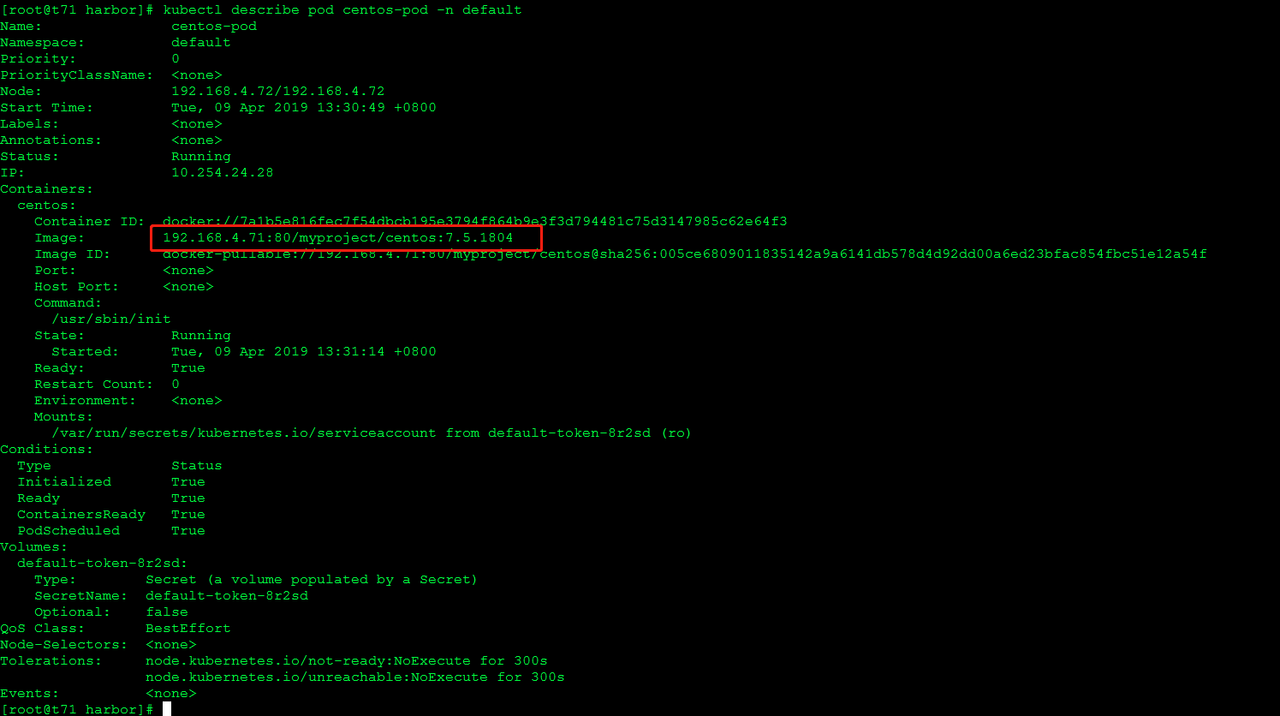
kubectl describe pod centos-pod -n default
2.1.4 查看web界面
2.1.5 上传image
[root@t71 harbor]# docker login 192.168.4.71:80
Username (zhangjx): zhangjx
Password:
Login Succeeded
[root@t71 harbor]# docker tag docker.io/progrium/consul 192.168.4.71:80/myproject/consul:latest
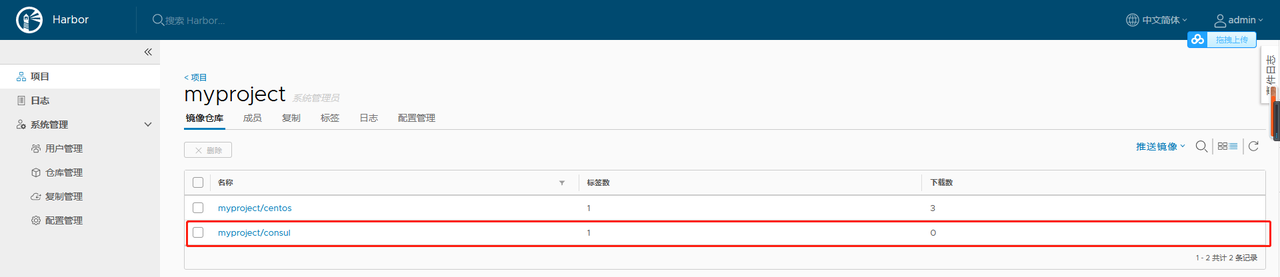
[root@t71 harbor]# docker push 192.168.4.71:80/myproject/consul:latest
The push refers to a repository [192.168.4.71:80/myproject/consul]
5f70bf18a086: Pushed
d46ded49a20c: Pushed
af8c1839c171: Pushed
18fc328d2a80: Pushed
655df57eba5d: Pushed
2472fd5d1e44: Pushed
33cdef66dc09: Pushed
f70996ac24ae: Pushed
e4b1687664d8: Pushed
70f8ad72ed07: Pushed
1feb7d205df9: Pushed
f3ab176661f3: Pushed
745737c319fa: Pushed
latest: digest: sha256:c715e8c8e37691d07a3007bc8211dd4218cef18006a12f57bffdea6518104ae6 size: 4067
[root@t71 harbor]#
2.1.6 查看
3. 需要注意的地方
需要给docker的启动项中添加insecure-registries参数,并重启docker
[root@t71 harbor]# cat /etc/docker/daemon.json
{ "insecure-registries":["192.168.4.71:80"] }
[root@t71 harbor]#